desktop as a service (DaaS)
What is desktop as a service (DaaS)?
Desktop as a service (DaaS) is a cloud computing offering in which a third party hosts the back end of a virtual desktop infrastructure (VDI) deployment.
With DaaS, desktop operating systems (OSes) run inside virtual machines on servers in a cloud provider's data center. All the necessary support infrastructure, including storage and network resources, also lives in the cloud. As with on-premises VDI, a DaaS provider streams virtual desktops over a network to a customer's endpoint devices, where end users can access these virtual desktops and the apps loaded into them through client software or a web browser.
How does desktop as a service work?
DaaS architecture is multi-tenant, and organizations purchase the service through a subscription model -- typically based on the number of virtual desktop instances used per month.
In the DaaS delivery model, the cloud computing provider manages the back-end infrastructure costs and maintenance responsibilities of deploying apps, data storage, backup, security and upgrades. Customers usually manage their own virtual desktop images, applications and security, unless those desktop management services are part of their subscription.
This article is part of
What is virtual desktop infrastructure? VDI explained
Typically, an end user's personal data is copied to and from their virtual desktop during logon and logoff, and access to the desktop is device-, location- and network-independent.
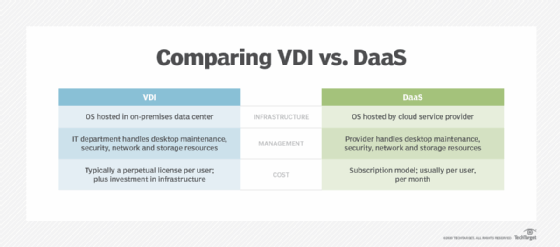
VDI vs. DaaS
Desktop as a service provides all the advantages of virtual desktop infrastructure, including remote worker support, improved security and ease of desktop management.
DaaS also aims to provide additional cost benefits. Deploying VDI in-house requires a significant upfront investment in compute, storage and network infrastructure. But those costs have decreased with the emergence of converged and hyper-converged infrastructure systems purpose-built for VDI.
With DaaS, on the other hand, organizations pay no upfront costs. They only pay for the virtual desktops they use each month. Over time, however, these subscription costs can add up and eventually be higher than the capital expenses of deploying on-premises VDI.
Additionally, some advanced virtual desktop management capabilities might not be available for certain DaaS deployments, depending on the provider.
Use cases for desktop as a service
The following are two potential use cases for desktop as a service:
Data security. When properly configured, DaaS can mitigate many of the security risks associated with physical devices, such as the risks posed by removable media.
Business continuity. DaaS lets employees access fully provisioned corporate desktop environments remotely so they can do their jobs without going into an office. Since the virtual desktops are hosted in the cloud and are accessible from anywhere, they could conceivably allow users to continue working after a disaster, as long as power and internet connectivity are available.
Persistent vs. nonpersistent DaaS desktops
Another important consideration of DaaS is the distinction between persistent and nonpersistent desktops.
A persistent desktop can be customized for a particular user, tweaked to the user's liking and able to save both their configuration and work. This requires more cloud storage in the service deploying the desktop, which can add to the cost of the subscription.
A nonpersistent desktop is created from scratch whenever a user loads it and is wiped when the user is done, saving nothing. This means no customization but can be less expensive.
Advantages of DaaS
Accessibility. DaaS and similar desktop virtualization technologies are accessible from anywhere, making them ideal for remote work. Organizations that subscribe to DaaS can provide their remote employees with a user experience that largely mimics that of users who are working onsite.
Scalability. Cloud service providers generally make it easy to scale up virtual desktop deployments. Because the virtual desktops are hosted on cloud infrastructure, organizations don't have to acquire and deploy additional physical hardware that's required when scaling on-premises VDI.
Cloud service providers also usually make it easy to scale down. For some organizations, this can potentially reduce license costs. For example, if an organization hires seasonal workers during certain times of the year, DaaS would allow it to easily provision cloud-based virtual desktops for the seasonal workers. Once the season is over, the organization can easily deprovision those virtual desktops, eliminating the costs associated with the virtual desktops.
Device-agnostic. DaaS lets users work from the device of their choosing. A user might choose to work from a PC, a Mac or a mobile device, as long as it has the necessary display resolution and remote desktop client software. The user's desktop environment is identical, regardless of the type of device they're using.
Reduces software license costs. For users who work from multiple devices, an organization can install an application onto a single virtual desktop, thereby consuming a single license, rather than installing the application onto each of the user's devices, which would require multiple licenses.
Simplifies disaster recovery. Rather than requiring IT to handle issues with potential desktop, laptop and device failures that can result in data loss, it consolidates all user data in an environment where a single disaster recovery model covers everything.
Easier to secure and maintain. If an employee's laptop or mobile device is stolen, it's easy to disconnect it from the service, breaking the link between the device and the data it can access. It's also easier to handle security patching and software updates in a DaaS cloud environment than it is to apply them to a large group of individual machines.
Reduces downtime. Companies that use DaaS can more easily provide remote IT support to their employees.
Disadvantages of DaaS
Increased OS license costs. License costs can increase when users access virtual desktops from company-owned desktops or laptops. In this case, a user's physical device would typically require an OS and the virtual desktop would require a second operating system license. However, most cloud service providers bundle the OS license cost into the cost of the virtual desktop.
Limited internet access. Because virtual desktops are hosted in the cloud, they must be accessed over the internet. If an organization experiences an internet outage, employees might be unable to access their desktops. Similarly, a user who is working from home over a slow internet connection might experience poor virtual desktop performance.
DaaS providers
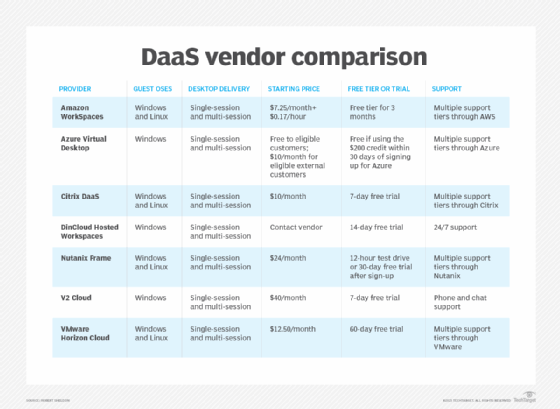
Before selecting a DaaS provider, organizations must do their homework, as not all DaaS services are the same. Decision-makers must ensure the cloud subscription provider meets both the users' and organization's needs.
The following table shows an overview of the different features, functionality and other factors organizations must consider before they select a DaaS provider.
Learn about additional pros and cons of DaaS when evaluating desktop virtualization options.






